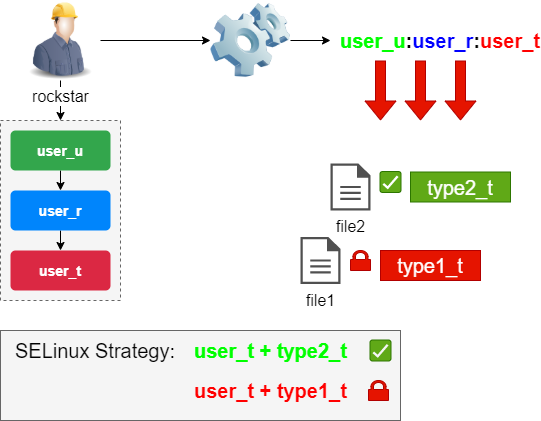
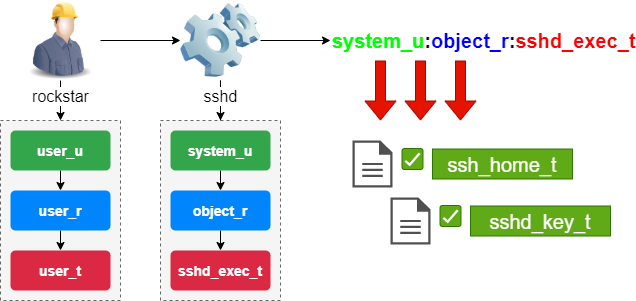
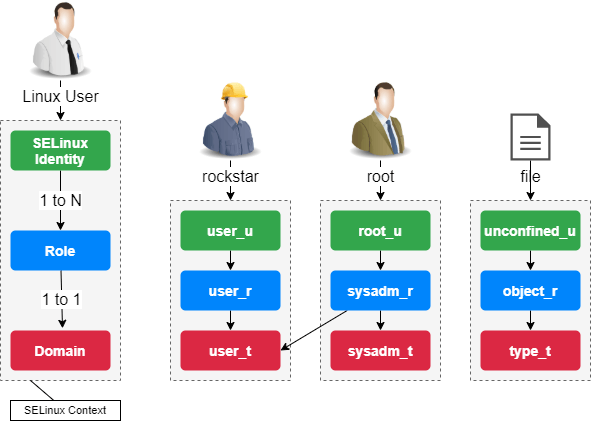
SELinux Overview ○ Permissions historically – Why is unix or ACL permissions not good enough? ○ DAC vs. MAC ○ SELinux ID, objects, roles and types ○ Policy. - ppt download

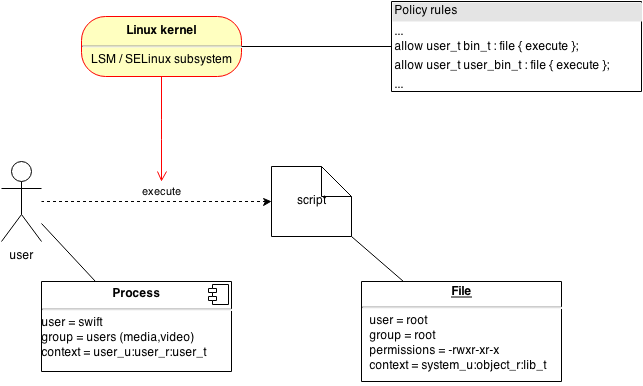
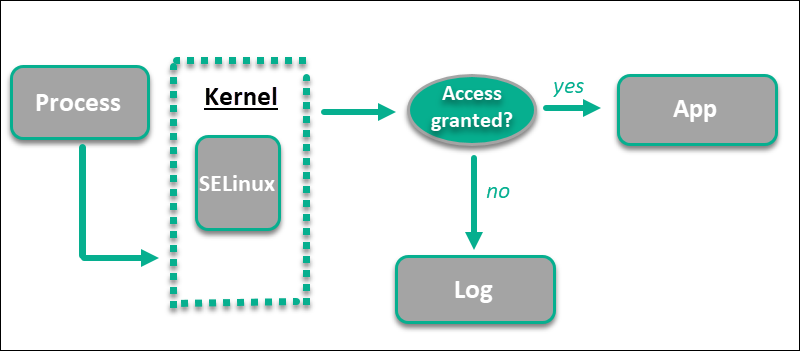
files - Are SELinux rules enforced before or after standard linux permissions? - Unix & Linux Stack Exchange



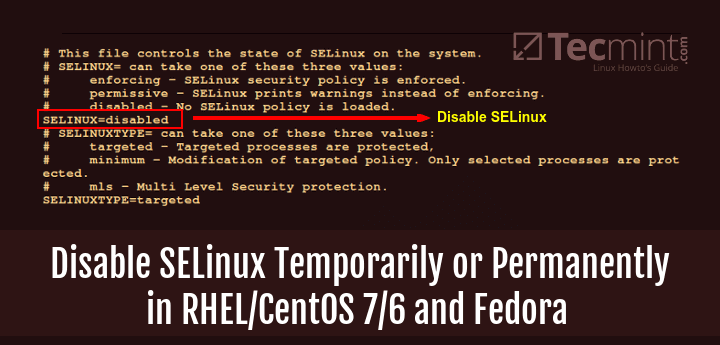
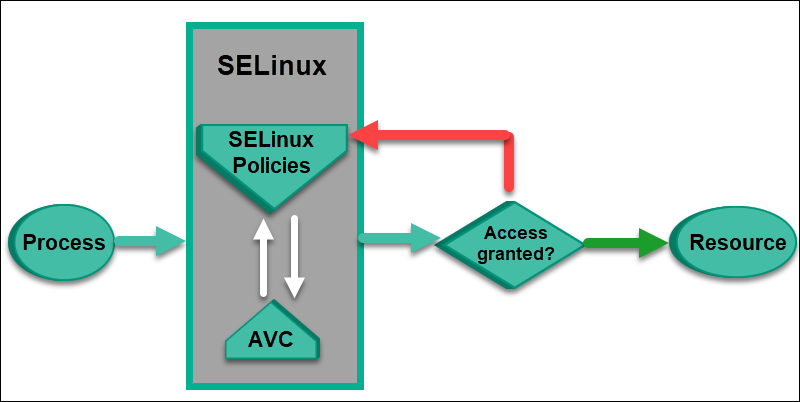
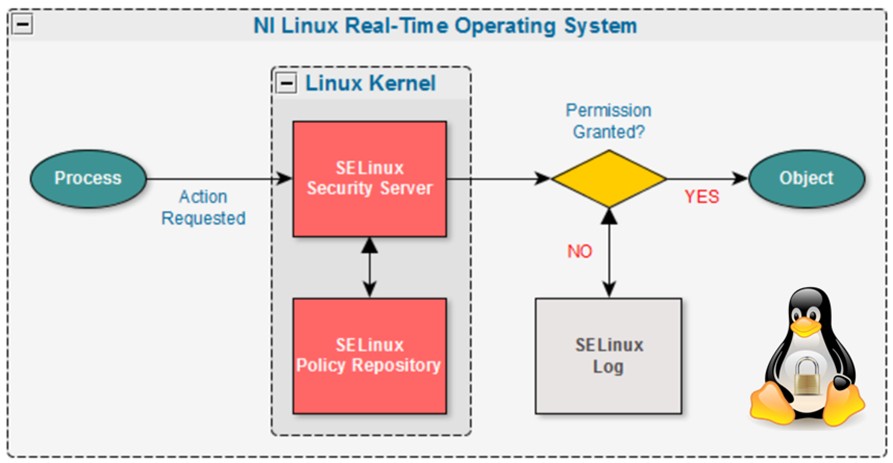
![Illustration] Introduction to SELinux – How it works? Explanation of the Basic knowledge – | SEの道標 Illustration] Introduction to SELinux – How it works? Explanation of the Basic knowledge – | SEの道標](https://milestone-of-se.nesuke.com/wp-content/uploads/2018/07/en-selinux-summary-1.png)