Tut03-2 Writing Exploits with Pwntools - CS6265 Information Security Lab.pdf - 9/12/22 11:17 AM Tut03-2: Writing Exploits with Pwntools - CS6265: | Course Hero
pwn asm' string format - not C style char array compatible & not matching output of hex format? · Issue #1109 · Gallopsled/pwntools · GitHub














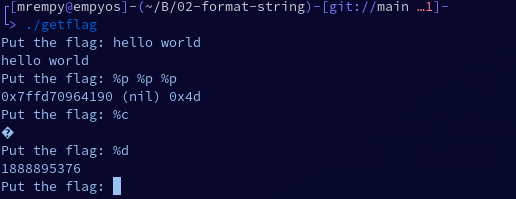


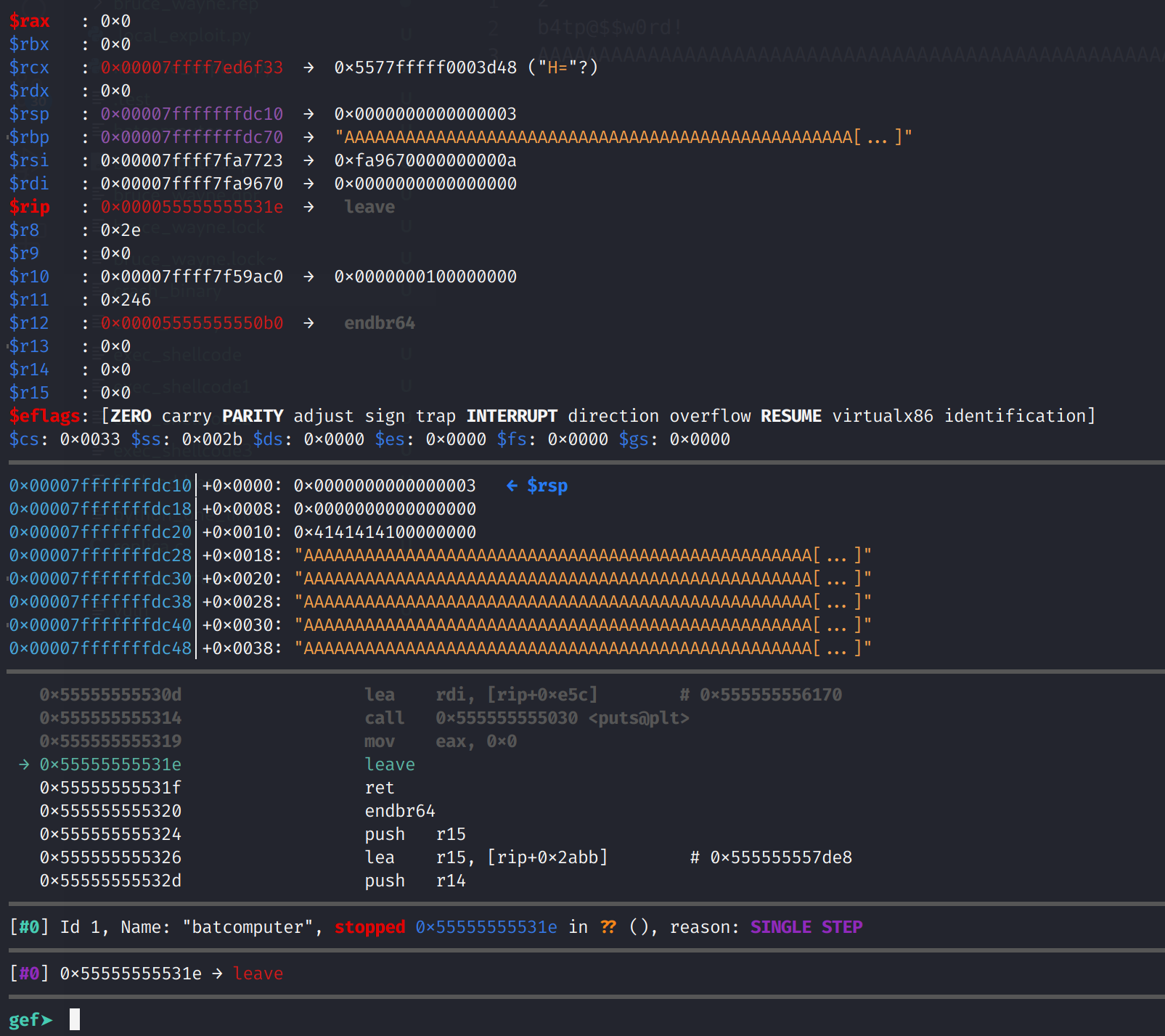
![Lab 07 - Strings [CS Open CourseWare] Lab 07 - Strings [CS Open CourseWare]](https://ocw.cs.pub.ro/courses/_media/cns/labs/info-leak-stack-64.png?w=600&tok=1285d8)