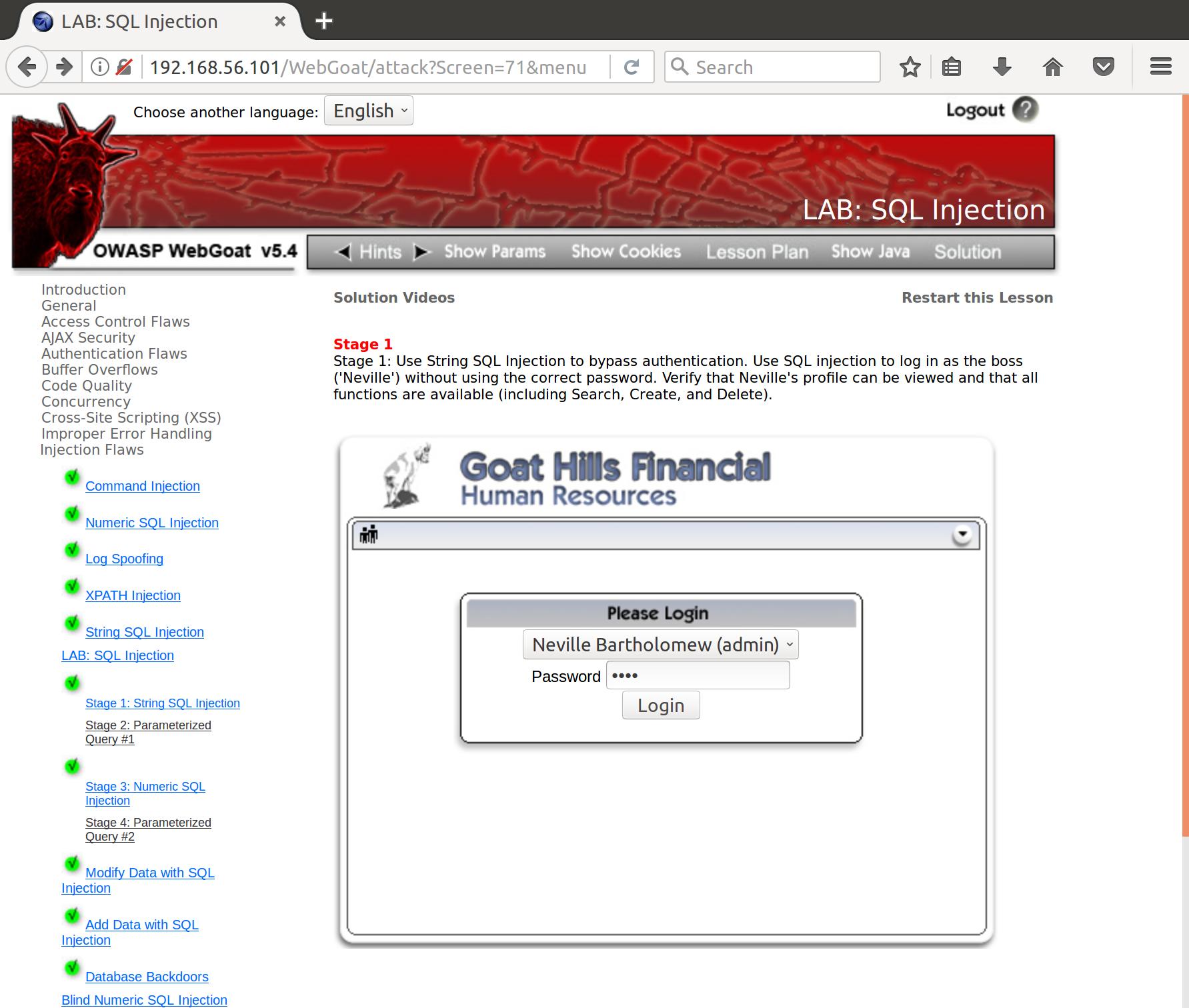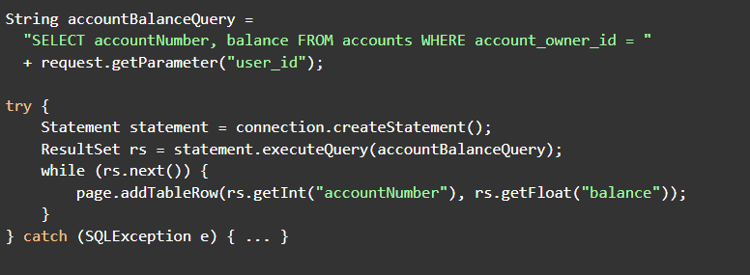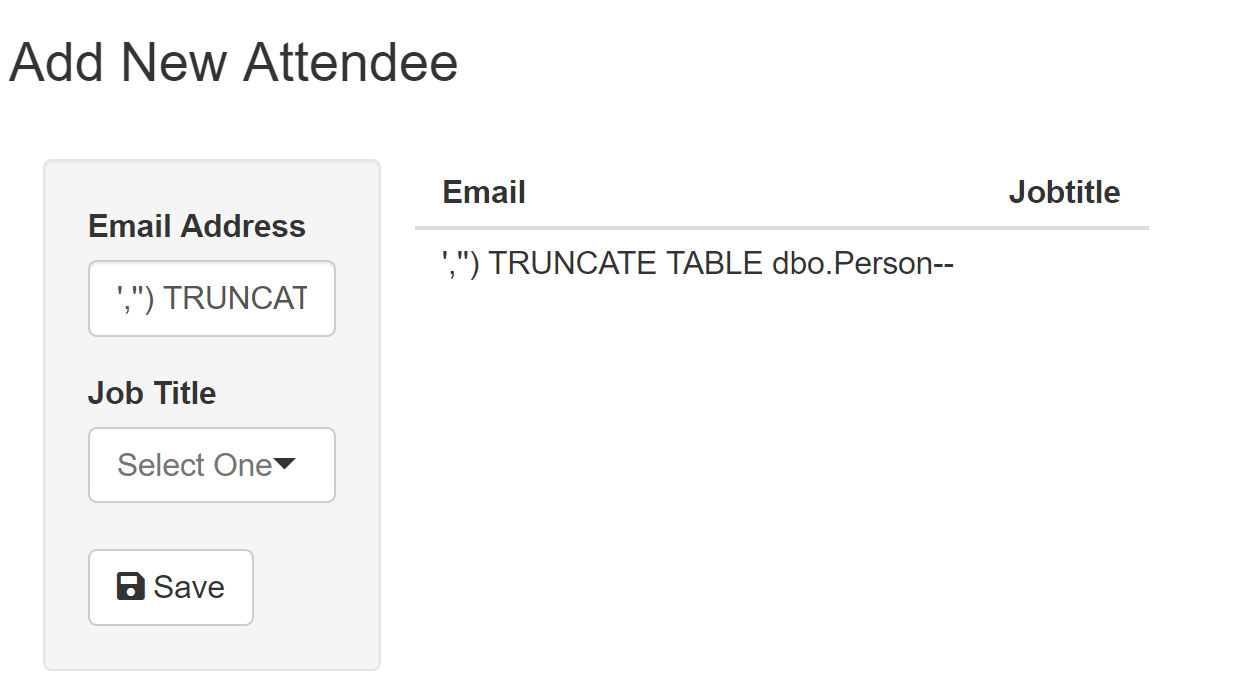
Energies | Free Full-Text | Study of the Failure Mechanism of an Integrated Injection-Production String in Thermal Recovery Wells for Heavy Oil

Collection Of Hand Holding String And Action Of Syringe, Hand Holding Syringe Injection And Hand Holding Condom Packet On White Background And Green Block For Easy To Select Stock Photo, Picture and